Understanding the ISMS Context
Purpose and Scope
The ISMS aims to safeguard Subnets’ information assets, establish a robust security framework, and ensure compliance with relevant regulations. The scope encompasses all company information and systems, including those used by employees, consultants, and suppliers.
Potential Impact of Security Incidents
A security breach can have severe consequences for Subnet, including financial losses, reputational damage, and legal liabilities. The ISMS aims to mitigate these risks through preventative measures, incident response plans, and continuous improvement efforts.
Organisational Context and Objectives
Business Activities
Subnets primary business activities include the design, build and execution of various Building Management Systems for the Data Centre, Pharmaceutical, Industrial & Commercial Sectors. The ISMS is designed to address the specific information security risks associated with these activities.
Strategic Objectives
The ISMS plays a vital role in Subnets ‘ strategic objectives for FY25 by ensuring data integrity, safeguarding sensitive information, and promoting operational efficiency.
Organisational Context and Objectives
Business Activities
Subnets primary business activities include the design, build and execution of various Building Management Systems for the Data Centre, Pharmaceutical, Industrial & Commercial Sectors. The ISMS is designed to address the specific information security risks associated with these activities.
Strategic Objectives
The ISMS plays a vital role in Subnets ‘ strategic objectives for FY25 by ensuring data integrity, safeguarding sensitive information, and promoting operational efficiency.
Risk Management and Appetite
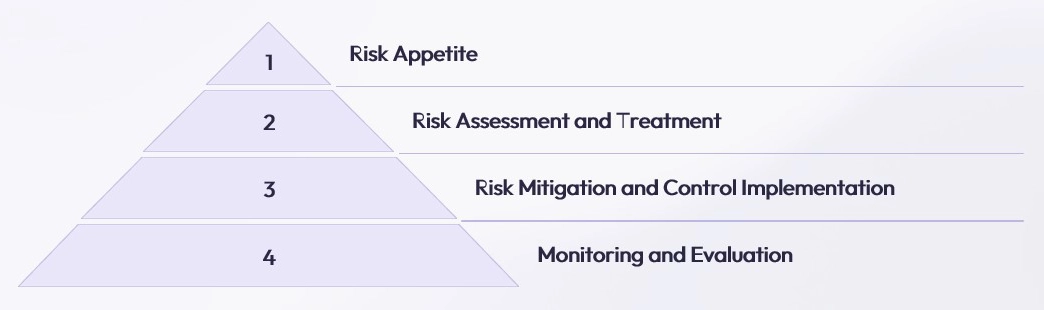
Subnet maintains a medium risk appetite, balancing the need for security with operational flexibility. The ISMS employs a comprehensive risk management framework, including identification, assessment, treatment, and ongoing monitoring to ensure that risks are managed within acceptable levels.
Interested Parties and Their Requirements
Senior Management Team
Senior management is responsible for setting information security policies, ensuring resource allocation for the ISMS, and promoting a culture of security awareness.
Employees
Employees are expected to comply with the ISMS, receive relevant training, and report security incidents promptly. They are also accountable for the secure use of company information and systems.
Suppliers
Suppliers must adhere to Subnets ‘ information security requirements, including contractual obligations and compliance with relevant ISMS protocols. They are also expected to maintain appropriate security controls within their own operations.
Legal and Regulatory Bodies
Subnet is subject to various legal and regulatory requirements related to information security, including GDPR, NCSC guidelines, and other relevant legislation. The ISMS ensures compliance with these regulations.
ISMS Implementation and Operation
1
The ISMS is implemented and maintained through a structured process, encompassing policy development, risk assessment, control implementation, and continuous monitoring and improvement
Subnet has defined a comprehensive set of information security policies, procedures, and guidelines that provide clear direction and guidance to all stakeholders.
2
3
Regular risk assessments are conducted to identify and analyze potential threats, vulnerabilities, and impact on Subnets’ information assets.
Appropriate controls are implemented to mitigate identified risks, ensuring the confidentiality, integrity, and availability of information.
4
5
The ISMS is subject to ongoing monitoring and review, including performance evaluations, internal audits, and management reviews to ensure its effectiveness and continuous improvement.
ISMS Monitoring and Evaluation
1. Control Effectiveness
The effectiveness of implemented controls is regularly evaluated against identified risks, ensuring that they are sufficient to mitigate the threats and vulnerabilities.
3. Management Reviews
Senior management conducts periodic reviews to assess the ISMS’ alignment with organizational goals, identify areas for improvement, and ensure its ongoing effectiveness.
2. Key Performance Indicators (KPIs)
Subnet has established KPIs to measure the ISMS’ performance, including incident response times, policy compliance rates, and other relevant metrics.
4. Continuous Feedback
Subnet gathers feedback from stakeholders, including employees, suppliers, and other interested parties, to identify areas for improvement and enhance the ISMS.
Internal Audits
1
Audit Planning
Subnet maintains a medium risk appetite, balancing the need for security with operational flexibility. The ISMS employs a comprehensive risk management framework, including identification, assessment, treatment, and ongoing monitoring to ensure that risks are managed within acceptable levels.
2
Execution
Internal audits are conducted by independent and qualified personnel to ensure impartiality and a thorough assessment of the ISMS’ implementation and effectiveness.
3
Corrective Actions
Corrective actions are implemented to address identified issues, with clear timelines and accountability to ensure prompt and effective resolution.
4
Audit Planning
Subnet maintains a medium risk appetite, balancing the need for security with operational flexibility. The ISMS employs a comprehensive risk management framework, including identification, assessment, treatment, and ongoing monitoring to ensure that risks are managed within acceptable levels.
5
Follow-Up
Subsequent audits are conducted to verify the effectiveness of implemented corrective measures and ensure ongoing compliance with the ISMS framework.
ISMS Documentation and Management
![]()
Policy and Procedure Development
Subnet maintains a comprehensive set of information security policies, procedures, and guidelines that cover all aspects of the ISMS.
 Controlled Distribution and Access
Controlled Distribution and Access
Access to ISMS documents is controlled and restricted to authorized individuals, ensuring confidentiality and the integrity of the information.
![]()
Revision and Approval Process
The ISMS is reviewed and updated on an annual basis, or whenever significant changes occur, ensuring its ongoing relevance and effectiveness.
 Training and Awareness
Training and Awareness
Employees receive ongoing training on the ISMS, including relevant policies, procedures, and their responsibilities related to information security.

1
Review and Evaluation
The ISMS is subject to continuous review and evaluation, ensuring that it remains aligned with evolving threats, industry best practices, and organizational needs.
2
Process Improvement
Subnet implements a proactive approach to process improvement, incorporating feedback from stakeholders, internal audits, and performance evaluations.
3
Technology Adoption
Subnet embraces new technologies and solutions to enhance information security, including advanced security controls, threat intelligence platforms, and incident response tools.
4
Stakeholder Engagement
Subnet fosters strong stakeholder engagement, seeking input and collaboration from employees, suppliers, and other interested parties to enhance the ISMS’ effectiveness.
ISMS Documentation and Management

![]()
Strong Commitment
Subnet demonstrates a strong commitment to information security, evidenced by the implementation of the ISO 27001:2022 compliant ISMS.
![]()
Stakeholder Engagement
The ISMS is built upon a foundation of stakeholder engagement, ensuring that all relevant parties are involved in its development, implementation, and ongoing improvement.
![]()
Comprehensive Framework
The ISMS is reviewed and updated on an annual basis, or whenever significant changes occur, ensuring its ongoing relevance and effectiveness.
![]()
Continuous Improvement
Subnet is committed to continuous improvement, ensuring that the ISMS adapts to evolving threats, technologies, and industry best practices.
ISMS Documentation and Management


